How to Stop WordPress Contact Form Spam: Proven Protection Methods
WordPress contact form spam affects nearly every website owner, with automated bots constantly targeting contact forms to send malicious links, advertisements, and meaningless messages. These spam submissions waste valuable time, clog email inboxes, and can even pose security risks to websites and their visitors.

The most effective way to stop contact form spam involves combining built-in spam protection methods with CAPTCHA solutions, anti-spam plugins, and advanced filtering techniques. Modern WordPress forms offer multiple layers of protection, from invisible background checks to user-friendly verification challenges that block automated submissions whilst allowing genuine enquiries through.
Understanding the various types of form spam and implementing the right combination of protection methods can eliminate over 99% of unwanted submissions. This comprehensive approach covers everything from basic WordPress security features to advanced bot mitigation tools, helping website owners choose the most suitable spam prevention strategy for their specific needs and technical expertise level.
Why WordPress Contact Form Spam is a Serious Issue

Contact form spam creates security vulnerabilities, damages site performance, and wastes valuable time for website owners. Spam entries can lead to malware infections whilst automated attacks overwhelm servers and mask legitimate customer enquiries.
Risks of Spam Submissions and Spam Bots
Spam bots actively crawl websites searching for vulnerable contact forms to exploit. These automated programmes inject malicious links that redirect users to phishing sites or revenue-generating advertisements.
When spam bots find contact forms, they launch brute force attacks against login systems. Successful attacks grant spammers complete control over WordPress websites.
Malware distribution represents another serious threat. Spammers install harmful software through compromised forms, putting both websites and visitors at risk.
Data theft becomes possible when attackers access sensitive customer information. Online shops face particular danger as spammers target payment details and personal data.
Email hijacking occurs when spammers use contact forms to send spam messages that appear to come from legitimate website owners. Recipients often trust these emails because they seem authentic.
This technique damages business relationships and brand reputation. Customers may lose trust when they receive suspicious emails that appear to originate from trusted companies.
Impact on Site Security and Performance
Server overload happens when thousands of spam entries flood contact forms simultaneously. Some websites receive over 18,000 spam attacks in a single night, overwhelming hosting resources.
Page loading speeds decrease significantly during spam attacks. Visitors experience slower websites, leading to higher bounce rates and lost conversions.
Database bloat occurs as spam entries accumulate in WordPress databases. These unnecessary records consume storage space and slow down database queries.
Security vulnerabilities multiply when spammers probe contact forms for weaknesses. They search for outdated plugins and unpatched security holes to exploit.
Website crashes become more likely during sustained spam attacks. High server loads can cause temporary outages that prevent legitimate users from accessing sites.
Hosting costs may increase as websites require additional resources to handle spam traffic. Some hosting providers charge extra fees for excessive resource usage.
Get Contact Form Spam Protection for Less than £1 per month!
Productivity and User Experience Concerns
Email inbox flooding forces website owners to sort through hundreds of fake enquiries daily. Real customer messages get buried beneath spam submissions, causing delayed responses.
Time wastage becomes significant as staff spend hours manually filtering spam instead of focusing on genuine business activities. This reduces overall productivity and increases operational costs.
Legitimate enquiries often get overlooked when spam overwhelms contact systems. Potential customers may not receive timely responses, leading to lost sales opportunities.
Email deliverability suffers when spam floods business inboxes. Important messages may be automatically filtered into spam folders by email providers.
Customer service quality declines when teams cannot efficiently manage genuine enquiries. Response times increase and customer satisfaction decreases.
Form abandonment increases when visitors encounter intrusive spam protection measures. Poor user experience can drive potential customers away from websites entirely.
Understanding Types of Contact Form Spam

Contact form spam comes in three main varieties, each requiring different prevention strategies. Spambots create automated submissions, humans send manual spam messages, and malicious actors use forms to distribute harmful links or malware.
Automated Spam and Spambots
Spambots are computer programs that automatically fill out contact forms. These bots scan websites looking for forms they can submit without human interaction.
Most spambots target simple forms because they lack proper security measures. They submit random text, promotional messages, or fake enquiries within seconds.
Automated spam makes up about 80% of all spam submissions. Bots often leave obvious signs like:
- Generic messages with poor grammar
- Submissions at unusual hours (2-4 AM)
- Multiple submissions from the same IP address
- Fields filled with random characters
Common spambot behaviours include submitting forms too quickly for human users. Real users typically spend 10-30 seconds filling out a contact form.
Some advanced bots can now solve basic puzzles. However, they still struggle with modern anti-spam protection and behaviour analysis tools.
Manual Spam Submissions
Manual spam comes from real people who deliberately send unwanted messages through contact forms. These submissions are harder to detect because they appear more human.
Human spammers often promote services, products, or websites through seemingly legitimate enquiries. They might offer SEO services, web design, or business opportunities.
Manual spam typically includes:
- Professional-looking messages
- Proper spelling and grammar
- Specific company names or contact details
- Links to external websites
These submissions take more effort to create but bypass many automated filters. Spammers often target specific industries or business types.
Some manual spammers use contact forms to test if email addresses are active. They send brief messages to see if they receive responses.
Geographic targeting is common with manual spam. Spammers research local businesses and tailor their messages to specific regions or markets.
Link and Malware Spam
Link spam uses contact forms to distribute harmful websites or malicious software. These submissions pose serious security risks beyond simple annoyance.
Malicious links often lead to phishing sites, malware downloads, or scam pages. Clicking these links can compromise user accounts or install viruses.
Common malware spam includes:
- Fake virus warnings
- Fraudulent payment notices
- Phishing attempts for login credentials
- Links to infected downloads
Some spam submissions contain embedded scripts or code designed to exploit website vulnerabilities. These attacks can damage websites or steal sensitive data.
Link spammers frequently disguise their intentions with legitimate-sounding messages. They might pose as potential customers whilst hiding malicious URLs in their signatures.
Modern browsers and email clients block many dangerous links automatically. However, new threats emerge regularly as spammers adapt their tactics.
Get Contact Form Spam Protection for Less than £1 per month!
Built-in Spam Protection Methods in WordPress
WordPress offers several built-in spam protection features that work automatically without requiring visitors to complete challenges. These methods include modern anti-spam tokens that validate legitimate submissions and honeypot fields that trick spam bots into revealing themselves.
Modern Anti-Spam Protection Features
Modern anti-spam protection uses invisible security tokens to validate form submissions. WPForms includes this feature as a built-in option that works silently in the background.
The system creates unique tokens for each form visit. When someone submits the form, the plugin checks if the token matches. Real visitors get valid tokens, whilst spam bots cannot generate them properly.
Key benefits of modern anti-spam protection:
- No impact on user experience
- Works automatically without setup
- Blocks most automated spam attempts
- Compatible with all browsers
To enable this feature in WPForms, users navigate to the form editor and click on Settings. Under Spam Protection and Security, they toggle on the modern anti-spam protection option.
This method stops spam without showing captchas or challenges to visitors. It runs behind the scenes and requires no additional configuration once enabled.
Honeypot Technique and Hidden Fields
The honeypot technique uses invisible form fields to catch spam bots. These hidden fields remain empty when real people submit forms, but bots often fill them out automatically.
Form builders create fields that are invisible to human visitors through CSS styling. The fields appear in the form code but not on the actual webpage. Legitimate users never see or interact with these fields.
How honeypot fields work:
- Hidden from real visitors using CSS
- Spam bots detect and fill the fields
- Plugin rejects submissions with filled honeypot fields
- No user interaction required
When a submission includes data in honeypot fields, the system automatically marks it as spam. This method effectively blocks automated spam submissions without affecting genuine users.
The honeypot technique works best alongside other spam protection methods. It catches basic spam bots but may not stop sophisticated attacks that analyse CSS styling.
Get Contact Form Spam Protection for Less than £1 per month!
Why This Method Also Enables WordPress User Registration Spam
It’s worth noting that exactly the same automated submission techniques used by bots to abuse contact forms are often applied to WordPress’s user registration system. Spammers write scripts that target the registration endpoint (e.g. /wp-login.php?action=register or custom registration pages), filling in usernames, email addresses, and even profile fields automatically.
Without protection, this allows them to generate large numbers of fake accounts that can be used for comment spam, backlink insertion, phishing, or other malicious activity. All the defenses you use for contact forms — honeypots, rate limiting, CAPTCHA or invisible bot detection, email verification — are just as essential on the registration side to prevent user registration spam.
Using CAPTCHA Solutions for Enhanced Security
CAPTCHA services provide powerful protection against automated spam bots by requiring users to complete verification challenges. Google reCAPTCHA offers multiple versions including v2 and v3 options, whilst hCaptcha presents privacy-focused alternatives with similar effectiveness.
Google reCAPTCHA: v2, v3, and Invisible Versions
Google reCAPTCHA remains the most popular CAPTCHA solution for WordPress contact forms. It offers three distinct versions to suit different security needs.
reCAPTCHA v2 comes in two formats. The checkbox reCAPTCHA v2 displays an “I’m not a robot” checkbox that users must tick. This version is simple and reliable for most websites.
The invisible reCAPTCHA v2 runs behind the scenes without showing challenges to most users. It analyses user behaviour patterns to detect bots automatically.
reCAPTCHA v3 uses advanced JavaScript to score user interactions. It assigns risk scores from 0.0 to 1.0 without interrupting the user experience.
The service is free for up to one million requests monthly. Setup requires creating site keys through Google’s admin console and configuring them in your form plugin.
Most form plugins like WPForms and Contact Form 7 include built-in reCAPTCHA integration. Users simply select their preferred version and enable it on specific forms.
hCaptcha and Alternative Verification Tools
hCaptcha provides a privacy-focused alternative to Google reCAPTCHA with similar spam protection capabilities. It collects less user data and offers charitable donation options from earnings.
The service displays image-based challenges that require users to identify objects or complete simple tasks. These challenges effectively block automated spam submissions.
hCaptcha offers better privacy compliance for websites concerned about data collection. It processes fewer personal details compared to Google’s services.
Cloudflare Turnstile presents another modern alternative that works invisibly in most cases. It challenges users only when suspicious behaviour is detected.
Setup for alternative CAPTCHA services follows similar steps to reCAPTCHA. Users create accounts, generate API keys, and configure them through their form plugins.
Most premium form plugins support multiple CAPTCHA providers. This allows website owners to switch between services based on their specific privacy and security requirements.
Implementing Custom CAPTCHA Fields
Custom CAPTCHA fields offer website owners greater control over spam prevention than standard solutions. These personalised verification methods can include mathematical equations, logic questions, or text-based challenges that bots struggle to solve.
Creating and Configuring Custom CAPTCHA
Most form builders include custom CAPTCHA field options in their advanced field selections. Users can typically find the custom CAPTCHA field under “Fancy Fields” or similar sections within their form builder interface.
The configuration process involves selecting the CAPTCHA type from available options. Mathematical CAPTCHAs present simple arithmetic problems like “5 + 3 = ?” that change with each page reload. Question-and-answer formats allow administrators to create specific queries relevant to their website or industry.
Setting up the field requires:
- Selecting the custom CAPTCHA field from the form builder
- Choosing between mathematical or question-based verification
- Customising the field label and description
- Testing the functionality before publishing
Mathematical CAPTCHAs work effectively because they generate new equations automatically. The system creates random problems that human users can solve easily whilst preventing automated submissions.
Question-based CAPTCHAs offer more personalisation options. Website owners can create questions about their business, location, or industry that genuine visitors would know.
Best Practices for Accessibility and Usability
Custom CAPTCHA implementation must consider users with disabilities and varying technical abilities. Clear instructions help all visitors understand what they need to complete.
Essential accessibility features include:
- Simple language in questions and instructions
- Large, readable fonts for mathematical problems
- Alternative text descriptions for screen readers
- Logical tab order for keyboard navigation
The difficulty level should remain appropriate for the target audience. Mathematical problems should use basic arithmetic rather than complex calculations. Questions must have obvious answers that don’t require specialised knowledge.
Testing the custom CAPTCHA field with real users reveals potential issues. Different browsers and devices may display the challenges differently. Regular monitoring ensures the system blocks spam whilst allowing legitimate submissions through successfully.
Avoid overly complicated questions that might frustrate genuine visitors. The goal is stopping bots without creating barriers for actual customers or users.
Cloudflare Turnstile and Advanced Bot Mitigation
Cloudflare Turnstile provides invisible protection against contact form spam whilst maintaining a smooth user experience. This system requires a Cloudflare account and offers both significant advantages and some limitations for WordPress users.
Setting Up Cloudflare Turnstile
Users need a Cloudflare account to access Turnstile services. The setup process begins by visiting the Cloudflare dashboard and navigating to the Turnstile section.
After logging into their Cloudflare account, users can register their WordPress site. This generates two essential keys: a Site Key and Secret Key. These credentials connect the website to Cloudflare’s bot protection system.
The integration process involves installing a compatible WordPress plugin. Popular options include:
- Simple Cloudflare Turnstile
- WPForms (with Turnstile support)
- Contact Form 7 extensions
- Fluent Forms
Users paste their Site Key and Secret Key into the plugin settings. The plugin then allows them to enable Turnstile protection on specific forms and pages.
Configuration options typically include login forms, registration pages, contact forms, and comment sections. The system works invisibly, running background checks without displaying puzzles or challenges to legitimate users.
Benefits and Limitations of Cloudflare Solutions
Cloudflare Turnstile offers several advantages over traditional CAPTCHA systems. It operates without cookies, making it GDPR-compliant by default. Users don’t see visual puzzles or distorted text, which improves form completion rates.
The system blocks bots before they reach the server, reducing resource usage. This helps maintain website performance even during automated attacks.
Key benefits include:
- Free service with robust protection
- No user interaction required
- Privacy-focused approach
- Real-time analytics dashboard
- Integration with other Cloudflare services
However, limitations exist. Some legitimate users behind strict corporate firewalls may experience issues. The system requires internet connectivity to Cloudflare’s servers for validation.
Advanced bots may occasionally bypass the protection, though this remains rare. Website owners should monitor their Turnstile dashboard for unusual patterns or failed validations that might indicate sophisticated attacks.
Get Contact Form Spam Protection for Less than £1 per month!
WordPress Anti-Spam Plugins and Tools
WordPress anti-spam plugins offer automated protection against unwanted form submissions by checking entries against databases of known spam sources and blocking malicious attempts before they reach your inbox. Leading solutions like Akismet, Jetpack, and Antispam Bee each provide different approaches to spam prevention with varying feature sets and pricing models.
Overview of Leading Anti-Spam Plugins
Akismet remains the most widely used WordPress anti-spam plugin. It comes pre-installed with WordPress installations and excels at filtering comment spam using its global database of spam sources. The plugin requires a subscription for commercial sites but offers free usage for personal blogs.
Jetpack provides comprehensive site management including anti-spam protection. Its spam filtering works across comments and contact forms whilst offering additional features like site statistics and security monitoring. The plugin connects sites to WordPress.com’s infrastructure for enhanced protection.
Antispam Bee stands out as a completely free alternative that focuses on privacy protection. This German-developed plugin processes all data locally without sending information to external servers. It blocks spam through multiple validation methods including IP checking and content analysis.
CleanTalk offers all-in-one protection for comments, contact forms, and user registrations. The plugin uses cloud-based filtering to block spam without requiring captchas, making it user-friendly whilst maintaining high effectiveness rates.
Key Features of Akismet, Jetpack, and Antispam Bee
Akismet Features:
- Automatic spam detection for comments and trackbacks
- Global database of over 500 billion spam attempts
- Spam queue management with easy review options
- False positive protection for legitimate comments
- Commercial site protection starting at £4 monthly
Jetpack Features:
- Combined spam protection and site management tools
- Contact form spam filtering alongside comment protection
- Real-time security monitoring and threat detection
- Site performance statistics and visitor insights
- Free basic plan with premium upgrades available
Antispam Bee Features:
- 100% free with no premium versions or subscriptions
- Local spam processing without external data sharing
- Country-specific blocking and IP-based filtering
- Honeypot technology to trap automated spam bots
- Statistics tracking within WordPress dashboard
- GDPR-compliant privacy protection
| Plugin | Best For | Pricing | Form Protection |
|---|---|---|---|
| Akismet | Comment spam | Free/£4+ monthly | Limited |
| Jetpack | All-in-one solution | Free/Premium tiers | Yes |
| Antispam Bee | Privacy-focused users | Completely free | Basic |
My Preferred Method
Myself, I use CleanTalk, it has a bunch of features that protect your contact forms from spam.
Here’s a glimpse of just a few things it can do:
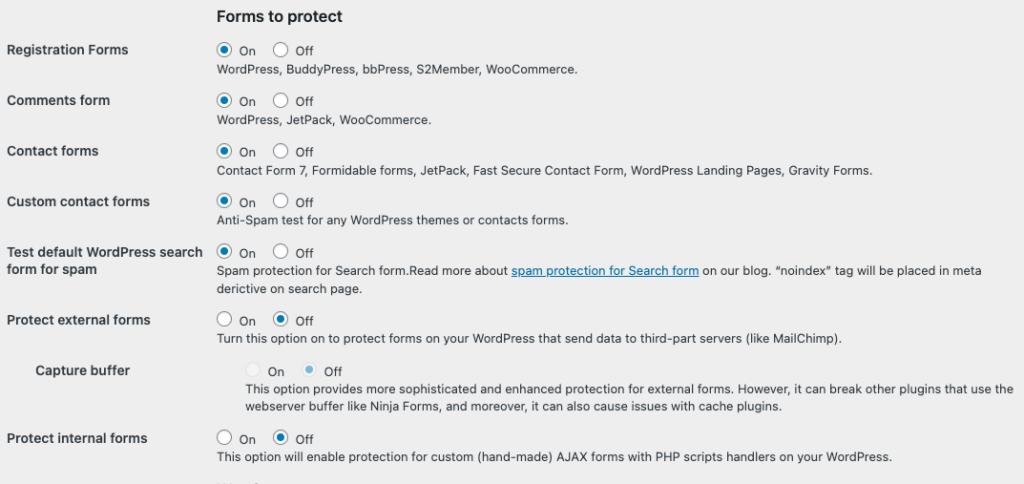
- Prevention of spam emails
- Email validation
- Geo-blocking
- Language blocking
- Email address protection
- Form spam filtering
- Integrates with most popular form plugins
I found it very easy to install CleanTalk:
1. Go to the WordPress plugin directory and search for the CleanTalk plugin
2. When you’ve found the plugin, install and activate it
3. Then go to the CleanTalk website and create an account
4. Register your website in the CleanTalk Account
5. From the CleanTalk console copy the access key
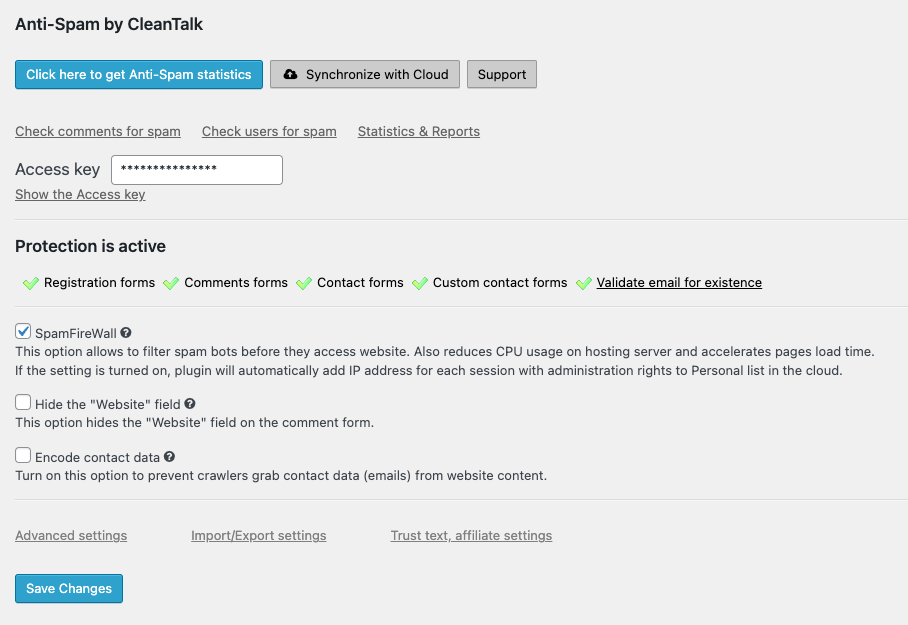
6. Go to the CleanTalk settings on your wp-admin panel
7. Paste the access key into the appropriate field
8. Save the settings
Installing CleanTalk will automatically put anti-spam features in place and clean your site of spam comments. I found it to be a quick install and also very beginner-friendly.
There are a number of advanced settings on the dashboard for the more experienced user.
Get Contact Form Spam Protection for Less than £1 per month!
Advanced Spam Prevention Techniques
These sophisticated methods provide additional layers of protection beyond basic CAPTCHA solutions. They work by analysing submission patterns, blocking problematic sources, and implementing timing controls to catch automated attacks.
Spam Filters and Keyword Blacklists
Spam filters automatically scan form submissions for suspicious content patterns and known spam indicators. These systems work by comparing incoming messages against databases of common spam phrases and malicious keywords.
Most WordPress form plugins include built-in keyword filtering. Administrators can create custom blacklists containing terms like “SEO services,” “crypto,” or “make money online.” The spam detection system blocks any submission containing these phrases.
Advanced filters also check for suspicious patterns:
- Multiple URLs in messages
- Excessive punctuation or capital letters
- Foreign language characters mixed with English
- Generic greetings like “Dear Sir/Madam”
Some plugins integrate with Akismet’s global spam database. This service analyses millions of spam submissions daily and shares threat intelligence across WordPress sites.
Setting Up Keyword Filters:
- Access form settings in your plugin
- Navigate to spam protection and security options
- Add problematic keywords to the blacklist
- Enable automatic filtering for suspicious patterns
Blocking IP Addresses and Countries
IP blocking prevents spam from specific sources by maintaining lists of problematic addresses. This method works well against persistent spammers who target sites repeatedly from the same locations.
WordPress security plugins can block individual IP addresses automatically when they detect spam patterns. They also support country-level blocking, which helps sites serving specific regions reduce international spam attacks.
Geographic restrictions work particularly well for local businesses. A UK-based company might block submissions from countries known for high spam activity whilst allowing legitimate traffic from their target market.
Common Blocking Strategies:
- Block known spam IP ranges
- Restrict submissions to specific countries
- Temporarily block IPs after multiple failed attempts
- Whitelist trusted IP addresses for important contacts
Many hosting providers also offer server-level IP blocking through their control panels.
Minimum Time Requirements and Timing Protections
Timing controls prevent automated bots from submitting forms too quickly. Real users need time to read and complete forms, whilst spam bots often submit within seconds of loading the page.
The minimum time requirement forces a delay between page load and submission. Most legitimate users take at least 10-15 seconds to complete a basic contact form. Setting this threshold blocks the majority of automated attacks.
Advanced timing protection also monitors submission patterns. Multiple rapid submissions from the same IP address trigger automatic blocking, even if individual submissions meet the minimum time requirement.
Recommended Timing Settings:
- Basic forms: 10-second minimum
- Detailed enquiries: 30-second minimum
- Application forms: 60-second minimum
Some plugins also implement maximum time limits. Forms submitted hours after loading may indicate suspicious activity, as legitimate users typically complete forms within reasonable timeframes.
These timing controls work invisibly in the background. Real visitors never notice the restrictions, whilst automated spam attacks fail immediately.
Email Verification and Deliverability Measures
Email verification tools can filter out fake addresses during form submission, whilst proper deliverability settings ensure legitimate contact form messages reach your inbox instead of spam folders.
Enforcing Email Confirmation
Email verification prevents spam by checking if email addresses are real before accepting form submissions. This method blocks bots that use fake or non-existent email addresses.
WordPress plugins can verify emails in real-time during form submission. They check if the email domain exists and if the address is formatted correctly.
Double opt-in verification requires users to confirm their email address through a verification link. This extra step stops automated spam bots completely.
Some verification tools check against databases of known disposable email services. These temporary email addresses are often used by spammers.
Benefits of email verification:
- Blocks fake email addresses instantly
- Reduces spam form submissions by 60-80%
- Protects your email sender reputation
- Prevents bounced emails from invalid addresses
Email verification works best when combined with other spam prevention methods. It creates multiple barriers that stop bots whilst allowing real users through.
Improving Form Notification Deliverability
Poor email deliverability means legitimate contact form messages end up in spam folders. This happens when your server’s sending reputation is damaged by spam.
SMTP authentication improves deliverability significantly. It sends emails through established email services instead of your web server.
WordPress transactional email plugins help ensure form notifications reach your inbox. They use services like SendGrid or Mailgun for better delivery rates.
Key deliverability factors:
- SPF records – Verify your domain can send emails
- DKIM signatures – Authenticate email content
- DMARC policies – Prevent email spoofing
- Dedicated IP addresses – Avoid shared server reputation issues
Contact form plugins should use proper email headers and formatting. This prevents legitimate notifications from triggering spam filters.
Regular monitoring of bounce rates and spam complaints helps maintain good sender reputation. High bounce rates from invalid addresses damage deliverability for all future emails.
Managing and Monitoring Spam Submissions
Even with prevention measures in place, some spam will slip through your defences. Site owners must know how to spot fake entries in their WordPress dashboard and establish routines to keep their forms clean and functional.
Identifying Spam Entries in the WordPress Dashboard
WordPress form plugins store submissions in the dashboard where administrators can review them. Most spam entries share common characteristics that make them easy to spot.
Generic or nonsensical content is the first red flag. Spam messages often contain random text, excessive links, or completely irrelevant content that doesn’t relate to your business.
Suspicious email addresses frequently appear in spam submissions. Look for:
- Random combinations of letters and numbers
- Multiple email addresses in one field
- Addresses from suspicious domains
- Missing @ symbols or malformed formats
Foreign characters or languages can indicate automated submissions, especially if they don’t match your target audience’s location or language preferences.
Promotional content often appears in spam entries. This includes unsolicited sales pitches, pharmaceutical advertisements, or offers for questionable services that legitimate visitors wouldn’t submit through contact forms.
Form timestamps can reveal bot activity. Multiple submissions within seconds or entries at unusual hours may indicate automated spam rather than genuine human contact.
Regular Form Maintenance and Entry Review
Successful spam management requires consistent monitoring routines. Site administrators should establish weekly or daily review schedules depending on their form submission volume.
Create a review checklist to streamline the process:
- Check submission times for unusual patterns
- Verify email addresses look legitimate
- Read message content for relevance
- Note any suspicious IP addresses
- Delete obvious spam immediately
Use filtering options in your WordPress dashboard to sort entries by date, email domain, or other criteria. This helps identify patterns and makes bulk deletion easier when necessary.
Keep legitimate entries organised by marking genuine submissions or moving them to separate folders. This prevents accidental deletion of real enquiries during spam cleanup.
Monitor your spam protection effectiveness by tracking how many spam entries reach your inbox versus those blocked automatically. If spam increases significantly, additional prevention measures may be needed.
Regular maintenance prevents spam from overwhelming your system and ensures genuine customer enquiries receive prompt attention.
Get Contact Form Spam Protection for Less than £1 per month!
Frequently Asked Questions
Contact form spam protection involves multiple layers of security including CAPTCHA systems, plugin-based filters, and form validation techniques. Modern solutions can block automated bots whilst maintaining a smooth experience for genuine users.
What methods can I implement to reduce spam submissions on my website’s contact form?
Several effective methods help reduce spam submissions on contact forms. CAPTCHA systems like Google reCAPTCHA or hCaptcha verify that real humans are submitting forms.
Built-in anti-spam protection filters suspicious submissions automatically. These systems run in the background without requiring user interaction.
IP address blocking prevents known spam sources from accessing forms. Country restrictions limit submissions to specific geographic regions if needed.
Email address filtering blocks or allows specific domains. This prevents spam from common throwaway email services.
Profanity filters reject submissions containing inappropriate language. These filters help maintain form quality and reduce unwanted content.
Are there any reliable plugins to help prevent spam in WordPress contact forms?
WPForms provides comprehensive spam protection with built-in modern anti-spam technology. The plugin includes CAPTCHA integration and automatic spam detection.
Akismet offers proven spam filtering that works across WordPress sites. This plugin identifies suspicious patterns and blocks fake submissions automatically.
Contact Form 7 includes basic spam protection features. However, it requires additional configuration and third-party services for advanced protection.
Gravity Forms includes anti-spam tools and honeypot fields. These features help detect and block automated bot submissions effectively.
How can I use CAPTCHA to protect my contact form from automated spam?
Google reCAPTCHA v2 shows a checkbox for users to tick. This method requires minimal user effort whilst blocking most automated bots.
Invisible reCAPTCHA v2 works behind the scenes without user interaction. The system analyses visitor behaviour to determine if they’re human.
reCAPTCHA v3 provides advanced protection using JavaScript detection. This version assigns risk scores to submissions and blocks suspicious activity.
hCaptcha offers privacy-focused protection with similar functionality to reCAPTCHA. This service collects less user data whilst maintaining effective spam blocking.
Setup requires registering your website with the CAPTCHA provider. You’ll receive site keys and secret keys to configure in your form plugin.
Can you recommend strategies for filtering out spam emails received through contact forms?
Keyword filtering blocks submissions containing common spam phrases. Create lists of suspicious words that trigger automatic rejection of submissions.
Email validation checks that submitted addresses use proper formatting. This prevents obviously fake email addresses from reaching your inbox.
Time-based restrictions limit how quickly forms can be submitted. Bots typically submit forms instantly, whilst humans take longer to complete them.
Form field limits restrict the length of text submissions. Spam messages often contain excessive text or links that exceed normal message lengths.
Honeypot fields remain hidden from human users but attract bots. When bots fill these fields, the system automatically rejects the submission.
What role does form validation play in deterring spam entries on my website?
Field validation ensures submitted data meets specific requirements. Required fields must be completed before forms can be submitted successfully.
Format validation checks that email addresses and phone numbers use correct patterns. Invalid formats get rejected automatically before submission.
Character limits prevent excessively long spam messages from being submitted. Most genuine enquiries stay within reasonable length boundaries.
Input sanitisation removes potentially harmful code from submissions. This prevents malicious scripts from being processed by your website.
Client-side validation provides immediate feedback to users about errors. Server-side validation provides additional security against sophisticated spam attempts.
Is it possible to block spam bots without hindering user experience on my contact form?
Modern spam protection works invisibly in the background. Users don’t see the security measures whilst genuine submissions pass through normally.
Smart CAPTCHA systems only appear when suspicious activity is detected. Most human users never encounter challenges during normal form submission.
Progressive enhancement adds security layers without breaking basic functionality. Forms remain usable even if advanced features fail to load.
Behavioural analysis tracks how users interact with forms. Genuine users scroll, pause, and type naturally, whilst bots submit instantly.
Risk scoring evaluates multiple factors to determine submission legitimacy. High-risk submissions face additional verification whilst normal users proceed unhindered.
Human-friendly error messages help genuine users correct mistakes. Clear instructions guide users through any required verification steps.
Author
-
Specialist in digital marketing for more than 18 years, I am the co-founder and CEO of T & T Web Design. Affordable Search Engine Optimisation (SEO), PPC Management and Reputation Management.
View all posts
Comments are closed.


